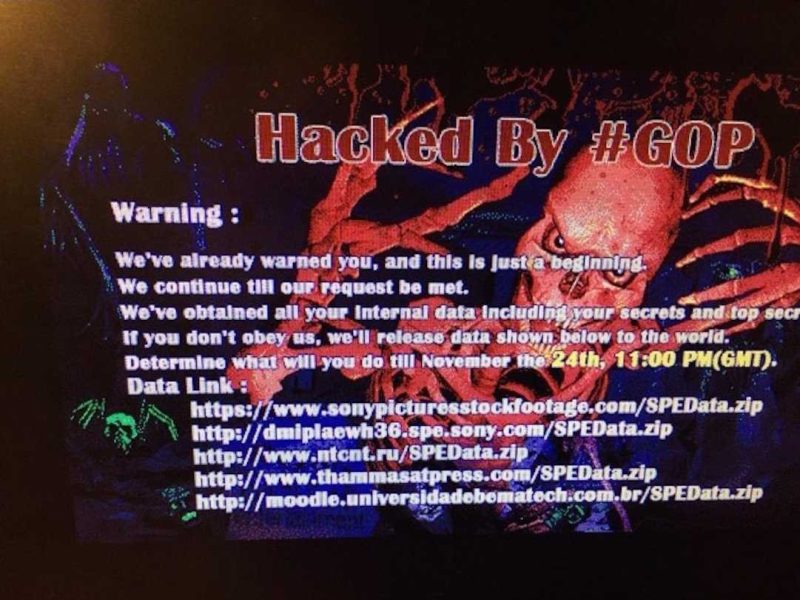
On November 24th, 2014, employees of Sony Pictures Entertainment arrived at the office as usual. Their humdrum expectations changed in an instant when a red skull splash page flashed onto their screens. Sony had been hacked. The day would be anything but typical.
The hackers, who identified themselves as the Guardians of Peace (GOP), stole thousands of confidential files and emails. Over a period of time, the hackers then leaked personal employee data and pirated copies of 5 unreleased movies. Communicating via the website Pastebin, they threatened acts of terrorism against movie theaters unless Sony cancelled the planned release of The Interview, a movie comedy about two Americans who assassinate Kim Jong Un, the leader of North Korea.
Consequences of the attack against Sony Pictures
Details of the attack have been explored thoroughly. The loss of corporate data, confidential information, and pre-releases of unpublished movies cost Sony an estimated thirty five million dollars. For months after the hack, Sony was subject to daily releases of confidential data posted on public websites and confidential data released to various media outlets. Even though the terrorist attacks did not manifest, the threat was real and highlighted the unforeseen consequences of weak network security.
Sony’s initial damage control measure was was to shut down the entire IT infrastructure. For several days, network administrators and database managers worked to restore from backup and to find and block the holes where the network leaks occurred.
How did the Sony hack occur?
How exactly did a multi-billion-dollar company like Sony Pictures fall prey to such an attack? How could they have prevented the breach? What was learned from this attack?
The hack may have happened when employees unwittingly click on phishing emails with malicious links. Hackers gain access through downloaded malware and compromised system security.
Shortly after the Sony attack, US-CERT said that attackers used a Server Message Block (SMB) Worm Tool to conduct attacks against a major entertainment company. Sony was not mentioned by name. Components of the attack included a listening implant, backdoor, proxy tool, destructive hard drive tool, and destructive target cleaning tool. The attack was successful but competing theories of state sponsored versus amateurish hackers who stumbled their way in are still found on various sites.
Database server records showed how the perpetrators got in. The malware had been siphoning data from Sony long before Sony learned of the hack. The hackers designed their code to target the specific Linux systems used on the network.
The almost daily leaks after the 2014 hack became a daily source of embarrassment for the Sony management team. Because the attack seemed well planned and executed, The FBI was quick to attribute the attack to North Korea. Years later, many Sony executives were not so sure.
Findings released to the FBI by Norse cyber security expert Kurt Stammberger suggest the hack was an inside job and included the statement,
“Sony was not just hacked; this is a company that was essentially nuked from the inside. We are very confident that this was not an attack master-minded by North Korea and that insiders were key to the implementation of one of the most devastating attacks in history.”
Stammberger believes that the security failure may have originated from six disgruntled former Sony employees. He argued that accessing and navigating selective information would take a detailed knowledge of Sony’s systems. Norse employees identified these people from a list of workers that were eliminated from Sony during a restructuring in May 2014. He noted that some had made very public and angry responses to their firing, and would be in appropriate positions to identify the means to access secure parts of Sony’s servers.
Why was Sony Pictures not prepared for the attack?
Sony planned to spend millions of dollars on upgrading their network and security systems and fixing all security loopholes after a 2011 PlayStation hacker attack. However, this did not go ahead. Senior executives felt that the funds required to secure the network were excessive considering the the perceived low risk of attack.
The IT department was not a revenue generator and so, instead, the IT workforce was reduced and fewer employees were allocated to manage security. Two ex-Sony employees revealed that the company knew that their systems were not secure, but management ignored the danger.
The sophistication of the attack and the care and effort that the attackers used to attack Sony, showed how ill-prepared Sony for the attack. Cybersecurity attacks are constant and continual. Shrewd investing in cybersecurity could have softened the blow and reduced financial losses.
What has been learned from the Sony Pictures attack?
Prioritize employee cyber-security training
A major factor in the Sony Pictures hack was lack of cybersecurity training. Hackers had also planned to strike the AMC Theatres with spoofed phishing emails. However, AMC had better protection measures and well-informed employees. This awareness saved AMC.
Security awareness training is critical in all companies. Hackers continue to find new and ingenious ways to mask their malware with genuine-looking emails incorporating inside information and corporate logos to fool even experience employees. One approach would be to hire white-hat penetration testing firms to seek out company vulnerabilities and weaknesses. A reward system is also a great way to motivate staff to enforce the measures and protocols.
Invest wisely in cyber-security
Companies of all sizes fall prey to hacker attacks. Fallout from an earlier attack in 2011 could (or should) have motivated Sony Pictures management to implement stricter cybersecurity measures. That the company did not have basic protections indicates, perhaps, how little Sony management understood the risks.
As a result of Sony’s failure to address its own security, hackers were able to transfer a large volume of data undetected. Limited secondary security around confidential data meant that the hackers could move slowly and thoroughly through the network and plan thefts that would cause the greatest destruction.
Secondary protective measures make it hard for hackers to get the information they need even after they have penetrated your network. If Sony had implemented internal network security measures, then the hack may have proved far less damaging and costly.
Hire highly-vetted employees in information security roles
The importance of highly qualified and trusted employees cannot be over-emphasized. Security needs have to be tailor-made to align with the company’s data and information structure. Whether some amateurish hackers found a back door or whether it was a dedicated North Korean attack is largely irrelevant. The real issue was that Sony under-invested in their network security.
Don’t plan security like the 2014 Sony Pictures Executive Team
The three years on from the April 2011 Playstation attack to the 2014 Sony Pictures attack was sufficient time to prepare for the any attack whether it would come from within or from without. There was more media outcry around the issue of attribution (who did it and why) and not so much about the issue of what could have been done to prevent it. The issue there is that Sony failed to prepare. And as the old adage goes, failing to prepare is preparing to fail.
Sources
- A breakdown and analysis of the December 2014 Sony Hack, December 5, 2014, RiskBased Security.
- FBI: North Korea to blame for Sony hack, December 19, 2014, Krebs on Security
- U.S.: No alternate leads in Sony hack, December 29, 2014, Politico
- FBI rejects alternate Sony hack theory, December 30, 2014, Politico
- The 2014 Sony Hacks, explained, June 3, 2015, Vox
- Five years later, who really hacked Sony? November 25, 2019, The Hollywood Reporter

